“Currently, we control your hospital. We own your servers. We own your systems. We own your patients’ medical records. To regain access to your medical records you need an encryption key...which only we have,” reads the hospital staff of Grey Sloan Memorial Hospital(1). In a pop culture nod, a mid-season finale episode of the television show Grey’s Anatomy titled “Out of Nowhere” depicts a cyber attack where hospital operations come to a halt as labs, monitors and patient files are compromised and held nonfunctioning by a hacker demanding $20 million be paid in a cryptocurrency called “bitcoin(1)." In the IT realm, this type of data breach is referred to as “ransomware.” Ransomware, specifically, is a relatively new type of computer virus that locks computer files and holds them hostage until a ransom has been paid(2). Ransomware has far-reaching and underestimated impacts in a digital age where the performance of essential day-to-day operations and protection of private information are dependent on technology functioning properly. Moreover, in the healthcare sector, the implications of this type of attack could range from loss of protected health information (PHI) stored in patient records to a complete disruption of clinical services, including incapacitating diagnostic equipment and lifesaving medications such as automated blood bank refrigerators(2).
Frighteningly, this media dramatization became very real for the victims of the ransomware attack on the Hollywood Presbyterian Medical Center on Feb. 5, 2016(3). Purportedly, the 434-bed facility’s computers were infected by a random malware attack inhibiting the staff from using any of their computers until a ransom of $17,000 was paid out. Per an interview with the hospital’s president and CEO Allen Stefanek, “The malware locks systems by encrypting files and demanding ransom to obtain the decryption key. The quickest and most efficient way to restore our systems and administrative functions was to pay the ransom and obtain the decryption key. In the best interest of restoring normal operations, we did this(3)." Furthermore, the $17,000 ransom request was met, ending a two-week long battle against a compromised network server, which locked staff out of email and hindered other various forms of electronic hospital communications(3). Mr. Stefanek was adamant that neither employee nor patient information was compromised during this cyber security breach(3).
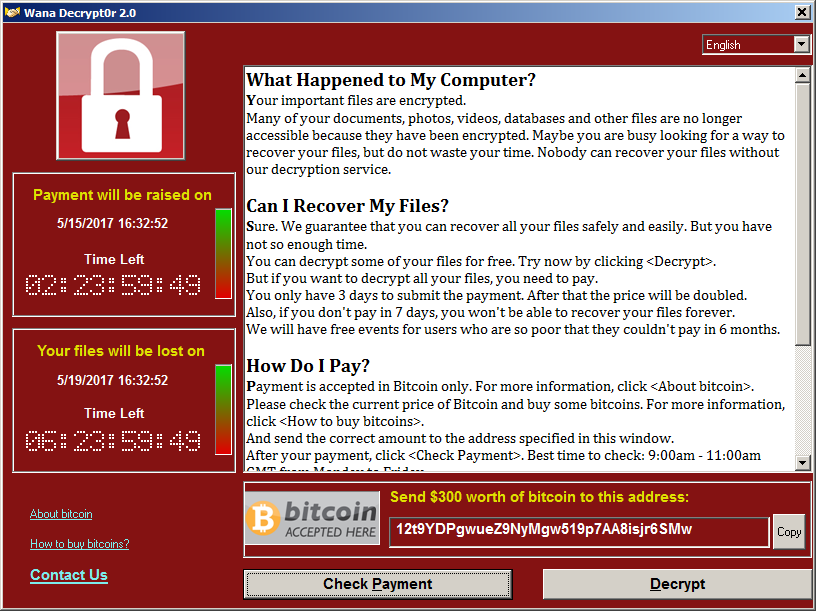
Figure 1. Screenshot of WannaCry Infected Computer. retrieved from:
https://commons.wikimedia.org/wiki/File:%EA%B0%90%EC%97%BC%EC%82%AC%EC%A7%84.png
In a second, even more significant event in 2017, the WannaCry ransomware virus hit the United Kingdom’s National Health Service (NHS). It infected vulnerable PC’s using outdated Microsoft Operating System technology (see Figure 1), hampering operations for 80 out of roughly 206 hospitals(4). The rapid spread of this virus resulted in cancelled appointments, disconnected diagnostic equipment, and an undisclosed number of outpatient surgeries and procedures that occurred, beginning May 12, 2017; and it also cost the NHS roughly £92m ($118m USD). The damages of this attack occurred over the course of a week(5). Initial efforts to determine the clinical impacts have shown no increase in patient mortality from the WannaCry attack, however, it is possible that patient harm occurred due to delays in treatment of time sensitive medical condition such as patients experiencing heart attacks, strokes or sepsis(4). Further research into the clinical impact of these events is critical to understand how best to protect patients from harm.
In the increasingly digital age of healthcare, cyber attacks are no longer a hypothetical risk seen only on TV. To ensure proper data protection and efficient and effective patient treatment, cyber security should never take a back seat, particularly in an increasingly paperless age. In the next few weeks, further elaboration will be given on the role of information technology disasters and their impact on the healthcare sector.
References:
- Fremont, Maggie. (2017, Nov. 17). Grey’s Anatomy Recap: Hacked. Retrieved from https://www.vulture.com/2017/11/greys-anatomy-recap-season-14-episode-8.html.
- Klimek, Mark. (2019, Sept. 17). Hospitals face rising risk of sophisticated cyberattacks. Retrieved from https://www.healthcarefinancenews.com/news/hospitals-face-rising-risk-sophisticated-cyberattacks.
- Winton, Richard. (2016, Feb. 18). Hollywood hospital pays $17,000 in bitcoin to hackers; FBI investigating. Retrieved from https://www.latimes.com/business/technology/la-me-ln-hollywood-hospital-bitcoin-20160217-story.html.
- Field, Matthew. (2018, Oct. 11). WannaCry cyber attack cost the NHS £92m as 19,000 appointments cancelled. Retrieved from https://www.telegraph.co.uk/technology/2018/10/11/wannacry-cyber-attack-cost-nhs-92m-19000-appointments-cancelled/.
- Smart, William. (2018, Feb. 11). Lessons learned review of the WannaCry Ransomware Cyber Attack. Department of Health and Social Care; Retrieved from: https://www.england.nhs.uk/wp-content/uploads/2018/02/lessons-learned-review-wannacryransomware-cyber-attack-cio-review.pdf.
- The George Washington University Hospital. (2020, Feb. 5). Emergency Medicine – Stroke, Heart Attack | GW Hospital. Retrieved from https://www.gwhospital.com/conditions-services/emergency-medicine.
- UpGuard, Inc. (2020, Feb. 5). Cerner Data Breaches, Cyber Attacks and Security Report. Retrieved from https://www.upguard.com/security-report/cerner.
- McGee, Marianne. (2019, Jan. 11). Boston Children's Hospital Hacker Gets Long Prison Sentence. Retrieved from https://www.bankinfosecurity.com/hacktivist-a-11932.

Justin Hull is a research fellow for Urgent Matters. A graduate in neuroscience from George Mason University. He is a medical scribe at George Washington Hospital while studying to get into medical school and has also scribed at Inova Fairfax Hospital ED.